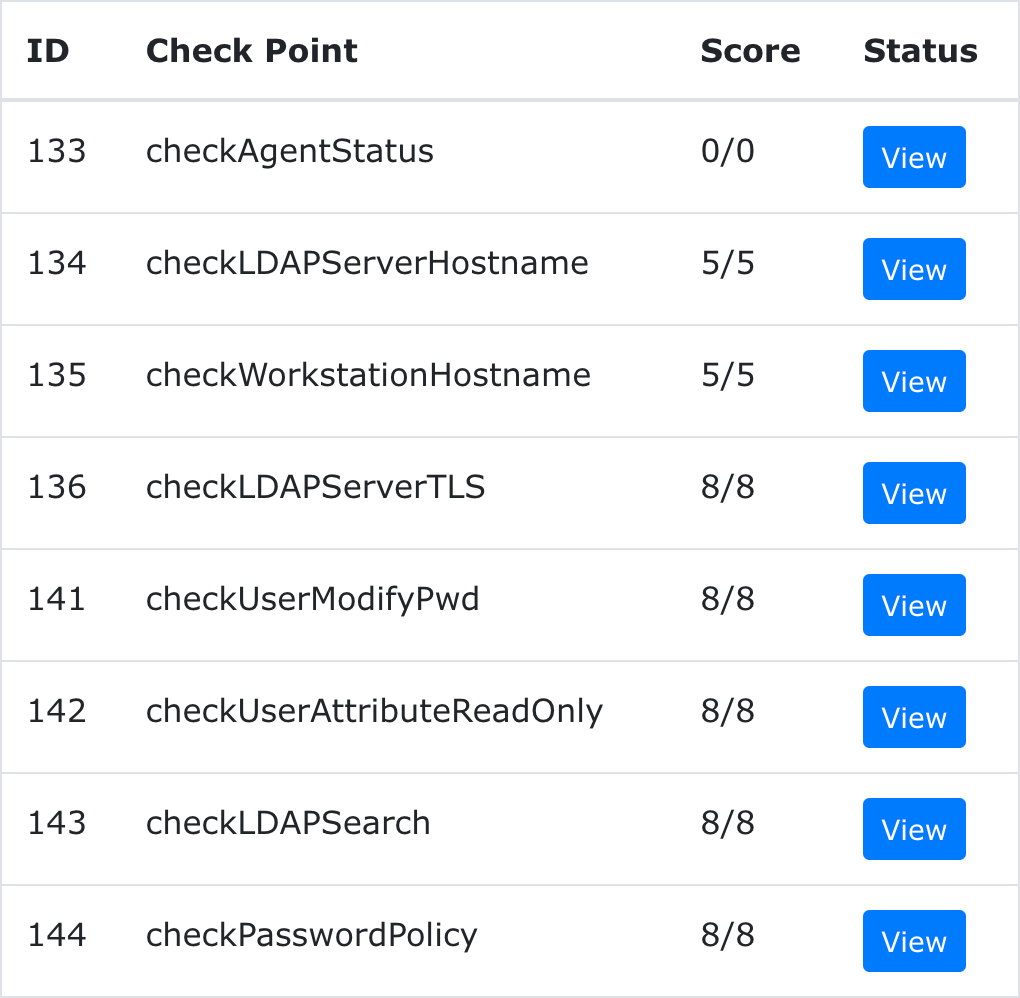
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
| ldapadd -D "cn=admin,dc=<ID>,dc=nasa" -w $pwd -ZZ
dn: ou=Group,dc=<ID>,dc=nasa
objectclass: organizationalUnit
ou: Group
dn: ou=People,dc=<ID>,dc=nasa
objectclass: organizationalUnit
ou: People
dn: uid=ta1,ou=People,dc=<ID>,dc=nasa
objectclass: account
objectclass: posixAccount
objectclass: shadowAccount
objectclass: ldapPublicKey
cn: ta1
uid: ta1
uidNumber: 10001
gidNumber: 10000
homeDirectory: /home/ta1
userPassword: <password>
sshPublicKey: <ssh-key>
dn: cn=ta,ou=Group,dc=<ID>,dc=nasa
objectclass: posixGroup
cn: ta
gidNumber: 10000
memberUid: 10001
dn: uid=stu<ID>,ou=People,dc=<ID>,dc=nasa
objectclass: account
objectclass: posixAccount
objectclass: shadowAccount
objectclass: ldapPublicKey
cn: stu<ID>
uid: stu<ID>
uidNumber: 200<ID>
gidNumber: 20000
homeDirectory: /home/stu<ID>
loginShell: /bin/bash
userPassword: <password>
dn: cn=stu,ou=Group,dc=<ID>,dc=nasa
objectclass: posixGroup
cn: stu
gidNumber: 20000
memberUid: 200<ID>
|