Spec
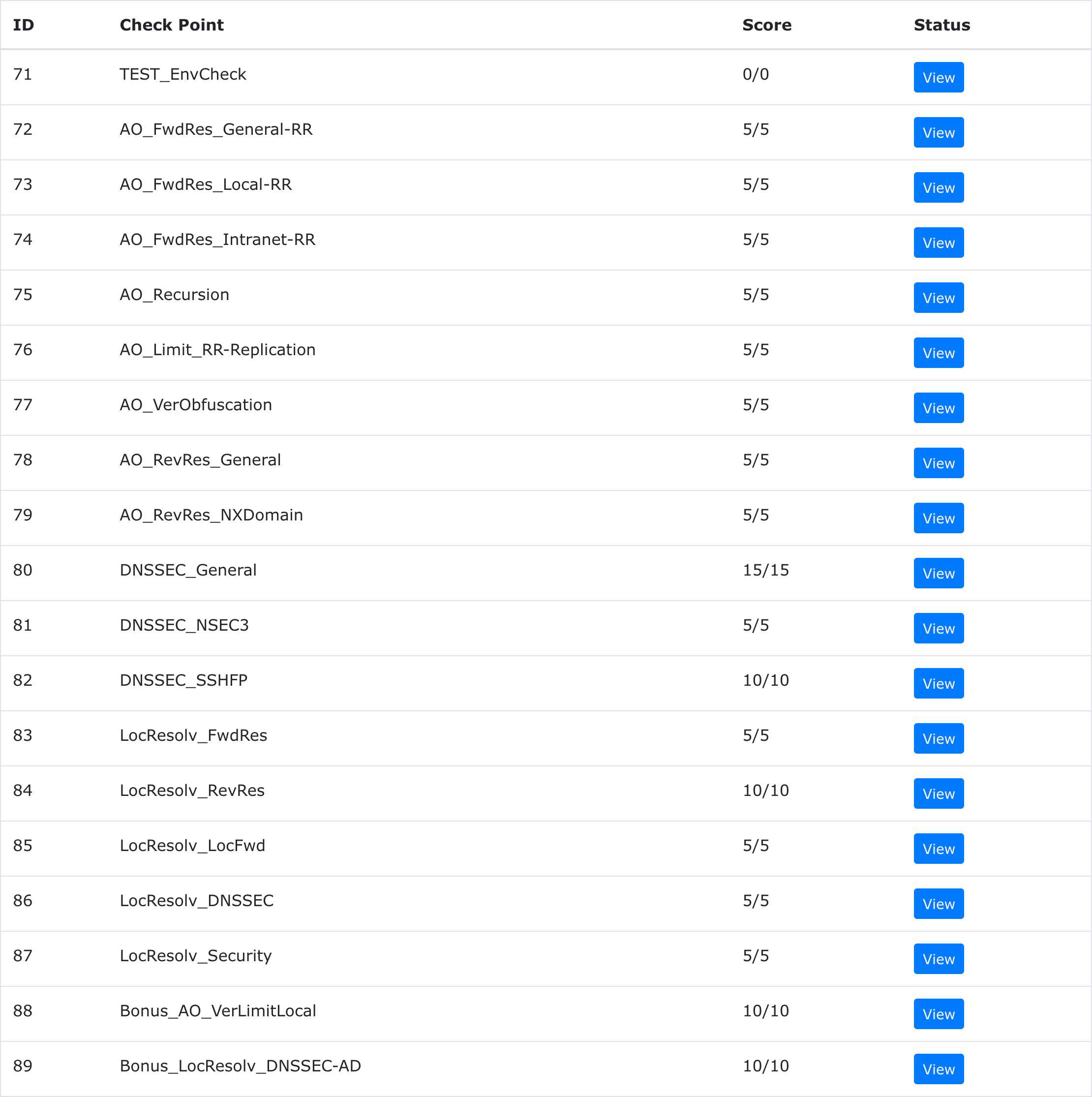
Check Point
Environment Setup 1
2
3
4
timedatectl set-timezone Asia/Taipei
apt install -y vim tmux htop tcpdump nload net-tools mtr
wget git.io/nella17-tmux-conf -O ~/.tmux.conf
wget https://github.com/nella17/dotfiles/raw/main/.vimrc.simple -O ~/.vimrc
install bind9 https://launchpad.net/~isc/+archive/ubuntu/bind
1
2
3
4
5
6
7
8
9
10
11
12
13
add-apt-repository ppa:isc/bind
apt update
apt install -y bind9
mkdir /etc/bind/db
mv /etc/bind/db.0 /etc/bind/db/rev.0
mv /etc/bind/db.127 /etc/bind/db/rev.127
mv /etc/bind/db.255 /etc/bind/db/rev.255
mv /etc/bind/db.empty /etc/bind/db/empty
mv /etc/bind/db.local /etc/bind/db/local
mkdir /etc/bind/keys
chmod 750 /etc/bind/keys
chown -R bind:bind /etc/bind
service named status
Note Reload named 1
2
3
4
5
# /etc/bind/named.conf
named-checkconf
service named restart
rndc reconfig
rndc reload
Check Log 1
2
service named status
journalctl -u named
Modify Zone File 1. via nsupdate 1
2
3
4
5
6
7
$ nsupdate
> server localhost
> ttl 3600
> add example.com. A 0.0.0.0
> del example.com. A 0.0.0.0
> show
> send
2. manual 1
2
3
4
5
6
7
8
9
# Freeze zone
rndc freeze
# Edit zone file
# Sign zone file
#- skip, using bind inline-signing
# Reload zone file
rndc reload
# Unfreeze zone
rndc thaw
Router firewall allow 53 port 1
2
iptables -A FORWARD -d 172.16.<ID>.1,172.16.<ID>.2,172.16.<ID>.10 -p udp --dport 53 -j ACCEPT
iptables -A FORWARD -d 172.16.<ID>.1,172.16.<ID>.2,172.16.<ID>.10 -p tcp --dport 53 -j ACCEPT
set dhcp DNS server 1
2
# /etc/dhcp/dhcpd.conf
option domain - name - servers 172.16 .< ID >. 10 ;
Authoritative-Only DNS Common named.conf 1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
acl LAN {
172.16 .< ID >. 0 / 24 ;
};
acl Trusted - NS {
172.16 .< ID >. 1 ;
172.16 .< ID >. 2 ;
172.16 .< ID >. 123 ;
};
options {
directory "/var/cache/bind" ;
allow - query { LAN ; };
allow - recursion { LAN ; };
allow - transfer { none ; };
allow - update { none ; };
recursion yes ;
serial - update - method unixtime ;
dnssec - validation auto ;
auth - nxdomain no ;
version "Name Server X" ;
};
TSIG Key 1
2
3
# on ns1
tsig-keygen -a hmac-sha256 <NAME> > /etc/bind/keys/<NAME>.key
# send key to ns2
Use 2 TSIG key to sync differnt view.
named.conf 1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
include "/etc/bind/keys/<NAME>.key" ;
# on ns1
server 172.16 .< ID >. 2 {
keys { < NAME > };
};
# on ns2
server 172.16 .< ID >. 1 {
keys { < NAME > };
};
# TSIG Control Access
view "Local" {
match - clients { ! key < NAME > ; };
};
view "Intranet" {
match - clients { key < NAME > ; };
};
primary - ns1 named.conf 1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
view "Local" {
match - clients {
key ns1 - ns2 - local .< ID >. nasa . ;
};
zone "<ID>.nasa" {
type primary ;
file "<ID>.nasa.local" ;
allow - query { any ; };
allow - transfer { any ; };
also - notify { 172.16 .< ID >. 2 key ns1 - ns2 - local .< ID >. nasa . ; };
key - directory "/etc/bind/keys/" ;
auto - dnssec maintain ;
inline - signing yes ;
};
};
view "any" {
match - clients { any ; };
zone "." {
type hint ;
file "/usr/share/dns/root.hints" ;
};
zone "<ID>.nasa" {
type primary ;
file "<ID>.nasa" ;
allow - query { any ; };
allow - transfer {
localhost ;
Trusted - NS ;
};
allow - update {
localhost ;
};
key - directory "/etc/bind/keys/" ;
auto - dnssec maintain ;
inline - signing yes ;
};
zone "<ID>.16.172.in-addr.arpa" {
type master ;
file "rev.<ID>.16.172" ;
allow - query { any ; };
allow - transfer {
localhost ;
Trusted - NS ;
};
allow - update {
localhost ;
};
};
};
Resource Record in /var/cache/bind/ 1
2
3
4
5
6
...
├── <ID>.nasa
├── <ID>.nasa.local
├── <ID>.nasa.shared
├── <ID>.nasa.sshfp
└── rev.<ID>.16.172
<ID>.nasa 1
2
3
4
5
6
7
8
9
10
$INCLUDE "<ID> .nasa.shared "
$ORIGIN <ID>. nasa.
@ NS ns1.<ID>. nasa.
NS ns2.<ID>. nasa.
A 172 . 16 .<ID>. 1
resolver A 172.16.254.10
router A 10 . 113 .<ID>. 1
<ID>.nasa.local 1
2
3
4
5
6
7
8
9
10
$INCLUDE "<ID> .nasa.shared "
$ORIGIN <ID>. nasa.
@ NS ns.<ID>. nasa.
A 172 . 16 .<ID>. 2
ns A 172 . 16 .<ID>. 2
resolver A 172 . 16 .<ID>. 10
router A 172 . 16 .<ID>. 254
<ID>.nasa.shared 1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
$ORIGIN .
$TTL 3600 ; 1 hour
<ID>.nasa IN SOA <ID>. nasa. root.<ID>. nasa. (
0 ; serial
86400 ; refresh (1 day)
1800 ; retry (30 minutes)
604800 ; expire (1 week)
7200 ; minimum (2 hours)
)
$ORIGIN <ID>. nasa.
$TTL 3600 ; 1 hour
ns1 A 172 . 16 .<ID>. 1
ns2 A 172 . 16 .<ID>. 2
agent A 172 . 16 .<ID>. 123
client A 172 . 16 .<ID>. 17
nasa CNAME nasa.cs.nctu.edu.tw.
$INCLUDE "<ID> .nasa.sshfp "
generate-reverse-zone.sh 1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
#!/bin/bash
ID = <ID>
prefix = "172.16. $ID ."
suffix = " $ID .16.172.in-addr.arpa."
file = "/var/cache/bind/rev. $ID .16.172"
if ! [ -e $file ] ; then
cat > $file << EOF
\$ORIGIN .
\$TTL 3600 ; 1 hour
$ID.16.172.in-addr.arpa. IN SOA $ID.nasa. root.$ID.nasa. (
0 ; serial
86400 ; refresh (1 day)
1800 ; retry (30 minutes)
604800 ; expire (1 week)
7200 ; minimum (2 hours)
)
NS ns1.$ID.nasa.
NS ns2.$ID.nasa.
\$ORIGIN $ID.16.172.in-addr.arpa.
EOF
rndc reload
fi
rr = ""
rr += $( dig @172.16.$ID .1 axfr $ID .nasa +noall +answer)
rr += $( dig @172.16.$ID .2 axfr $ID .nasa +noall +answer)
add = ""
while read line; do
type = $( echo $line | cut -d' ' -f4)
if [ " $type " = "A" ] ; then
ip = $( echo $line | cut -d' ' -f5)
domain = $( echo $line | cut -d' ' -f1)
if [[ " $ip " = " $prefix " * ]] ; then
k = $( echo $ip | cut -d'.' -f4)
add += "add $k . $suffix 3600 IN PTR $domain \n"
fi
fi
done <<< " $rr "
rr = ""
rr += $( dig @172.16.$ID .1 axfr $suffix +noall +answer)
# rr+=$(dig @172.16.$ID.2 axfr $suffix +noall +answer)
del = ""
while read line; do
type = $( echo $line | cut -d' ' -f4)
if [ " $type " = "PTR" ] ; then
del += "del $line \n"
fi
done <<< " $rr "
payload = "server localhost\n"
payload += " $del "
add = " $( echo -ne $add | sort -r | sort -h -u -k2,2) "
while read line; do
payload += " $line \n"
done <<< " $add "
payload += "show\n"
payload += "send\n"
nsupdate < <( echo -ne $payload )
secondary - ns2 & local - ns named.conf 1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
view "Local" {
match - clients {
! key ns1 - ns2 .< ID >. nasa . ;
key ns1 - ns2 - local .< ID >. nasa . ;
localhost ;
LAN ;
};
zone "." {
type hint ;
file "/usr/share/dns/root.hints" ;
};
zone "<ID>.nasa" {
type secondary ;
primaries { 172.16 .< ID >. 1 key ns1 - ns2 - local .< ID >. nasa . ; };
file "<ID>.nasa.local" ;
allow - transfer {
localhost ;
Trusted - NS ;
Trusted - Client ;
};
};
zone "<ID>.16.172.in-addr.arpa" {
type secondary ;
primaries { 172.16 .< ID >. 1 ; };
file "rev.<ID>.16.172" ;
allow - query { any ; };
};
};
view "Intranet" {
match - clients {
key ns1 - ns2 .< ID >. nasa . ;
any ;
};
zone "<ID>.nasa" {
type secondary ;
primaries { 172.16 .< ID >. 1 ; };
file "<ID>.nasa" ;
allow - query { any ; };
};
zone "<ID>.16.172.in-addr.arpa" {
in - view Local ;
};
};
DNSSEC 1
2
3
4
5
6
7
8
9
ID = <ID>
cd /etc/bind/keys
dnssec-keygen -a RSASHA256 $ID .nasa.
dnssec-keygen -a RSASHA256 -f KSK $ID .nasa.
chown bind:bind K*.key K*.private
# set custom nsec3param
rndc signing -nsec3param 1 0 10 140113 $ID .nasa [ IN Local]
# generate DS record, uploda to parent zone
dig @localhost DNSKEY $ID .nasa | dnssec-dsfromkey -2 -f - $ID .nasa
SSHFP 1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
#!/bin/bash
ID = <ID>
f = /var/cache/bind/$ID .nasa.sshfp
echo > $f
rr = $( dig @ns.$ID .nasa $ID .nasa AXFR +noall +answer)
while read line; do
type = $( echo $line | cut -d' ' -f4)
if [ $type = "A" ] ; then
domain = $( echo $line | cut -d' ' -f1)
ssh-keyscan -D $domain >>$f
fi
done <<< " $rr "
Local Resolver DNSKEY from TLD 1
dig @172.16.254.1 nasa DNSKEY +noall +answer +multiline
named.conf 1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
acl VPN {
10.113 . 0.0 / 16 ;
172.16 . 0.0 / 16 ;
};
acl VPN - TA - LAN {
10.113 . 0.0 / 24 ;
};
acl VPN - LAN {
10.113 .< ID >. 0 / 24 ;
};
acl LAN {
172.16 .< ID >. 0 / 24 ;
};
primaries NASA - NS {
172.16 . 254.1 ;
};
primaries 14 - NASA - NS {
172.16 . 14.2 ;
# 172.16.14.1;
};
trust - anchors {
nasa . static - key ( DNSKEY from TLD );
};
options {
directory "/var/cache/bind" ;
allow - query {
LAN ;
VPN - LAN ;
VPN - TA - LAN ;
};
recursion yes ;
dnssec - validation auto ;
version none ;
};
zone "." {
type hint ;
file "/usr/share/dns/root.hints" ;
};
zone "nasa" {
type stub ;
primaries { NASA - NS ; };
};
zone "16.172.in-addr.arpa" {
type stub ;
primaries { NASA - NS ; };
};
zone "14.nasa" {
type stub ;
primaries { 14 - NASA - NS ; };
};
zone "14.16.172.in-addr.arpa" {
type stub ;
primaries { 14 - NASA - NS ; };
};
Question 1. NS1 notify NS2 sync zone fail In NS2, use view to serve different RR for local & intranet, NS1 belong to internal view, but secondary at external view.
Not good solution: Make NS1 belong to external view.
Control access via TSIG Key.
2. Sync local view & intranet view ? Move local view to NS1, use TSIG sync to NS2.
3. Zone Transfer timeout AXFR use TCP, allow TCP:53 from router.
4. Judge Timeout Check before submit, make cache at DNS server to prevent timeout.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
#!/bin/bash
set -x
ID = <ID>
echo
echo "!!!! AO !!!!" >/dev/null
echo "---- AO_FwdRes_General-RR ----" >/dev/null
dig @172.16.$ID .1 +short nasa.$ID .nasa CNAME
dig @172.16.$ID .2 +short nasa.$ID .nasa CNAME
dig @172.16.$ID .1 +short agent.$ID .nasa
dig @172.16.$ID .2 +short agent.$ID .nasa
echo "---- AO_FwdRes_Local-RR ----" >/dev/null
dig @172.16.$ID .2 +short router.$ID .nasa
dig @172.16.$ID .2 +short $ID .nasa
dig @172.16.$ID .2 +short resolver.$ID .nasa
echo "---- AO_FwdRes_Intranet-RR ----" >/dev/null
dig @172.16.$ID .1 +short router.$ID .nasa
dig @172.16.$ID .1 +short $ID .nasa
dig @172.16.$ID .1 +short resolver.$ID .nasa
echo "---- AO_Recursion ----" >/dev/null
dig @172.16.$ID .1 +short nasa.$ID .nasa
dig @172.16.$ID .2 +short nasa.$ID .nasa
echo "---- AO_Limit_RR-Replication ----" >/dev/null
dig @172.16.$ID .1 +short $ID .nasa AXFR
dig @172.16.$ID .2 +short $ID .nasa AXFR
echo "---- AO_VerObfuscation ----" >/dev/null
dig @172.16.$ID .1 +short version.bind TXT CH
dig @172.16.$ID .2 +short version.bind TXT CH
echo "---- AO_RevRes_General ----" >/dev/null
dig @172.16.$ID .1 +short -x 172.16.$ID .1
dig @172.16.$ID .1 +short -x 172.16.$ID .2
dig @172.16.$ID .1 +short -x 172.16.$ID .254
dig @172.16.$ID .1 +short -x 172.16.$ID .10
dig @172.16.$ID .2 +short -x 172.16.$ID .1
dig @172.16.$ID .2 +short -x 172.16.$ID .2
dig @172.16.$ID .2 +short -x 172.16.$ID .254
dig @172.16.$ID .2 +short -x 172.16.$ID .10
echo "---- AO_RevRes_NXDomain ----" >/dev/null
dig @172.16.$ID .1 +noall +comments -x 172.16.$ID .77 | grep NX
dig @172.16.$ID .2 +noall +comments -x 172.16.$ID .77 | grep NX
echo
echo "!!!! DNSSEC !!!!" >/dev/null
echo "---- DNSSEC_General ----" >/dev/null
dig @172.16.$ID .10 +noall +comments +dnssec $ID .nasa | grep ad
echo "---- DNSSEC_NSEC3 ----" >/dev/null
dig @172.16.$ID .10 +short $ID .nasa NSEC3PARAM
dig @172.16.$ID .10 +noall +authority +dnssec x.$ID .nasa
echo "---- DNSSEC_SSHFP ----" >/dev/null
dig @172.16.$ID .10 +short +dnssec agent.$ID .nasa SSHFP
echo
echo "!!!! LocalResolv !!!!" >/dev/null
echo "---- LocResolv_FwdRes ----" >/dev/null
dig @172.16.$ID .10 +short ta.nasa
dig @172.16.$ID .10 +short ta.nasa NS
dig @172.16.$ID .10 +short ns.ta.nasa
dig @172.16.$ID .10 +short nasa.cs.nctu.edu.tw
dig @172.16.$ID .10 +noall +authority nasa.cs.nctu.edu.tw NS
dig @172.16.$ID .10 +short cs.nctu.edu.tw NS
echo "---- LocResolv_RevRes ----" >/dev/null
dig @172.16.$ID .10 +short -x 172.16.254.10
dig @172.16.$ID .10 +short 254.16.172.in-addr.arpa. NS
dig @172.16.$ID .10 +short -x 140.113.17.32
dig @172.16.$ID .10 +short 17.113.140.in-addr.arpa. NS
dig @172.16.$ID .10 +short cs.nctu.edu.tw NS
echo "---- LocResolv_LocFwd ----" >/dev/null
dig @172.16.$ID .10 +short router.$ID .nasa
dig @172.16.$ID .10 +short $ID .nasa
dig @172.16.$ID .10 +short resolver.$ID .nasa
echo "---- LocResolv_DNSSEC ----" >/dev/null
dig @172.16.$ID .10 +noall +comments +dnssec ta.nasa | grep ad
echo "---- LocResolv_Security ----" >/dev/null
# need test from other LAN
echo
echo "!!!! Bounus !!!!" >/dev/null
echo "---- Bonus_AO_VerLimitLocal ----" >/dev/null
# need test from other LAN
echo "---- Bonus_LocResolv_DNSSEC-AD ----" >/dev/null
dig @172.16.$ID .10 +noall +comments +dnssec $ID .nasa | grep ad
Refs