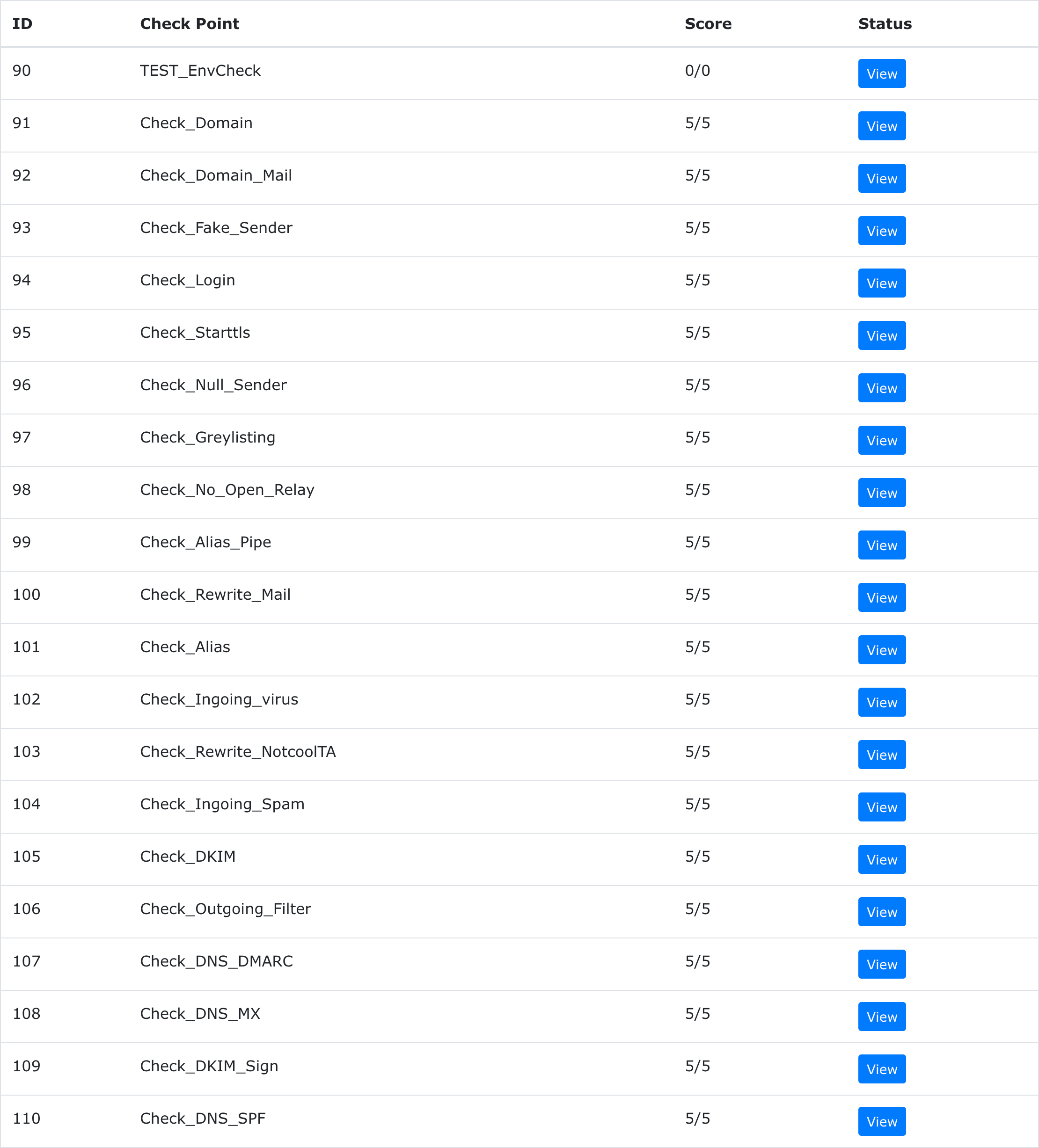
Spec
Check Point
Environment Setup
Allow ports on Router
| |
prepare develop tools
| |
Setup & Utils
Generate SSL Key Pair
| |
Create virtual home
| |
User & Pass
| |
Users
| |
Backup & Diff conf
| |
DNS Record
| |
Mail Server - Postfix
https://launchpad.net/~isc/+archive/ubuntu/bind
| |
/etc/postfix/main.cf
| |
/etc/postfix/master.cf
| |
Maps
| |
Generate maps/{file}.db
| |
header_checks
| |
relay_recipients
| |
sender_access
| |
sender_canonical
| |
sender_login
// 0 = ID
| |
valias-regexp
| |
virtual_alias-hash
| |
virtual_alias-pcre
| |
virtual_mailbox
| |
IMAP & Auth Server - Dovecot
| |
/etc/dovecot/conf.d/10-master.conf
| |
/etc/dovecot/conf.d/10-mail.conf
| |
/etc/dovecot/conf.d/10-ssl.conf
| |
/etc/dovecot/conf.d/10-auth.conf
| |
/etc/dovecot/conf.d/auth-passwdfile.conf.ext
| |
Greylisting - Postgrey
| |
TODO: move Greylisting to rspamd
Spam Scan - amavis + spamassassin + clamav
| |
Amavisd-new
/etc/amavis/conf.d/05-node_id
| |
/etc/amavis/conf.d/15-content_filter_mode
| |
/etc/amavis/conf.d/20-debian_defaults
| |
/etc/amavis/conf.d/21-ubuntu_defaults
| |
/etc/amavis/conf.d/50-user
| |
ClamAV
/etc/clamav/clamd.conf
| |
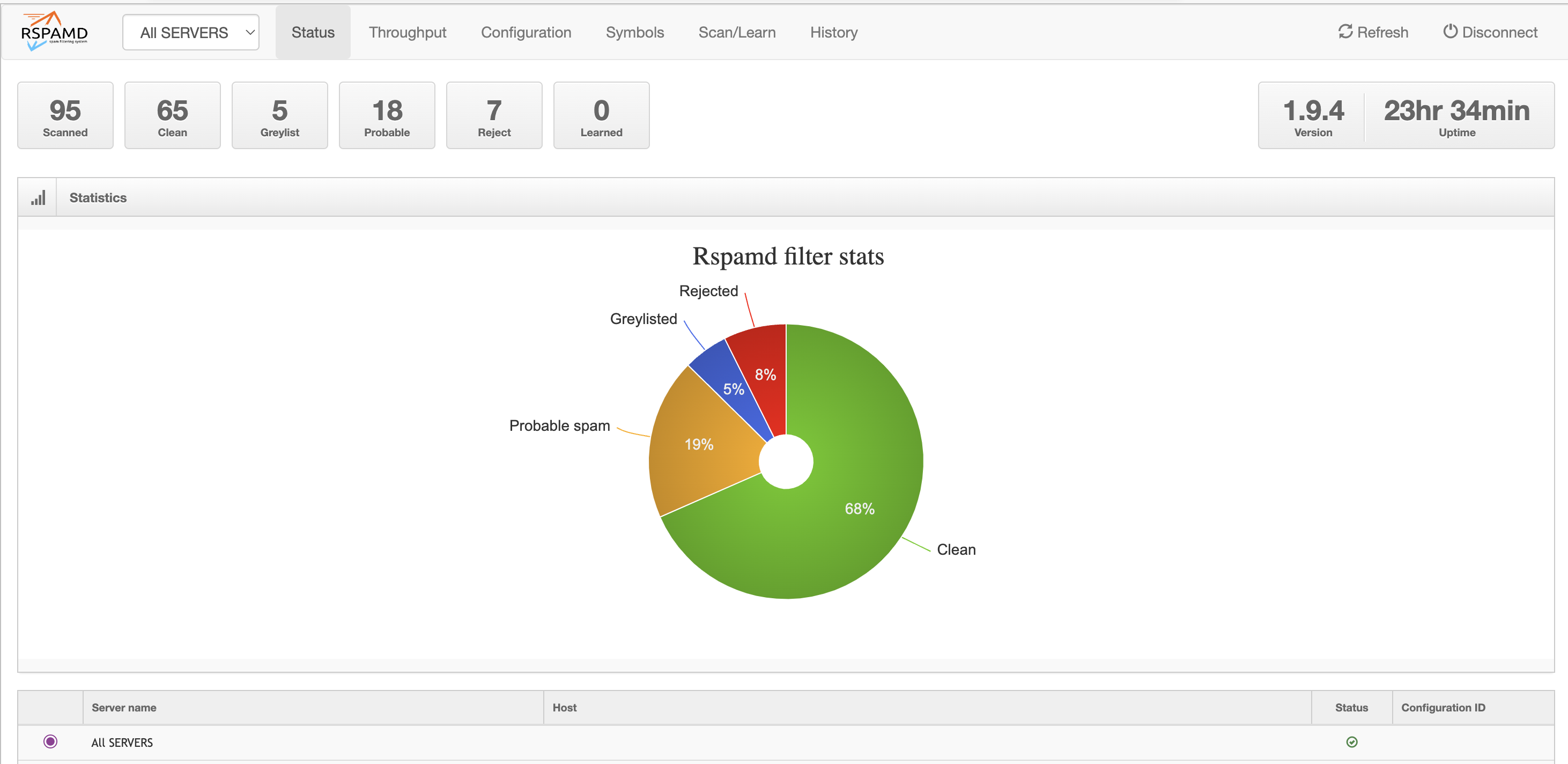
All in one tool - Rspamd
- Greylisting
- DKIM
- Spam scan
- Web UI Statistics
- Better config location
| |
Config Structure
default path:
/etc/rspamd$LOCAL_CONFDIR/local.d/file.conf- to add your options or rewrite defaults
$LOCAL_CONFDIR/override.d/file.conf- to override the defaults
/etc/rspamd/local.d/actions.conf
| |
/etc/rspamd/local.d/antivirus.conf
| |
/etc/rspamd/local.d/dkim_signing.conf
| |
/etc/rspamd/local.d/milter_headers.conf
| |
/etc/rspamd/local.d/spamassassin.conf
| |
/etc/rspamd/local.d/worker-controller.inc
| |
/etc/rspamd/local.d/worker-proxy.inc
| |
Testing
Mutt
| |
~/.muttrc
| |
Postfix
soft_bounce = yes
dovecot
/etc/dovecot/conf.d/10-logging.conf
Questions
// missing …